Paint on Your iPad | Color
Updated: 2012-10-31 17:07:57
via vimeo.com Posted via email from danielmiessler.com | posterous
 My Behavior Model shows that three elements must converge at the same moment for a behavior to occur: Motivation, Ability, and Trigger. When a behavior does not occur, at least one of those three elements is missing. via behaviormodel.org Posted via email from danielmiessler.com | posterous
My Behavior Model shows that three elements must converge at the same moment for a behavior to occur: Motivation, Ability, and Trigger. When a behavior does not occur, at least one of those three elements is missing. via behaviormodel.org Posted via email from danielmiessler.com | posterous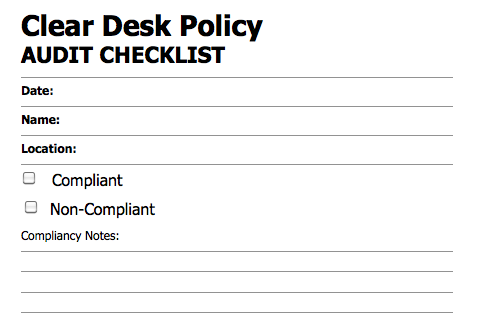 A Clear Standard
A Clear Desk Policy is becoming a more commonly adopted STANDARD ...(more)...
A Clear Standard
A Clear Desk Policy is becoming a more commonly adopted STANDARD ...(more)...  I need some help designing my new logo. It’s going to be super simple–circular with something in the center that represents me or the site. [ Ok, so I think I'm going to go with the tree. Does anyone have the graphics skills to put a nice symmetrical tree in to this graphic? ] Here [...]
I need some help designing my new logo. It’s going to be super simple–circular with something in the center that represents me or the site. [ Ok, so I think I'm going to go with the tree. Does anyone have the graphics skills to put a nice symmetrical tree in to this graphic? ] Here [...] In a new report by 451 Research, the enterprise IT innovation firm our new VAST program is highlighted for it's ability to lower the barriers of application security testing for enterprises. Says CEO Bob Brennan;
"VAST was created to increase the security of buying software. We work with enterprises to define the level of security they should expect and then we work with their vendors to see that those expectations are met."
In a new report by 451 Research, the enterprise IT innovation firm our new VAST program is highlighted for it's ability to lower the barriers of application security testing for enterprises. Says CEO Bob Brennan;
"VAST was created to increase the security of buying software. We work with enterprises to define the level of security they should expect and then we work with their vendors to see that those expectations are met." We recently hosted a webinar featuring Chenxi Wang of Forrester Research Inc and Chad Holmes of Veracode that discussed how enterprises can better understand and reduce security risks associated with using vendor-supplied software. This blog post will highlight the key takeaways of the webinar.
We recently hosted a webinar featuring Chenxi Wang of Forrester Research Inc and Chad Holmes of Veracode that discussed how enterprises can better understand and reduce security risks associated with using vendor-supplied software. This blog post will highlight the key takeaways of the webinar.  :
: A short while ago I stumbled onto the Twitter account of an Information Security Awareness program at my alma mater the Rochester Institute of Technology (RIT). I was immediately impressed by the following they had among their social networks and after digging a bit deeper into their activities I couldn't help but reach out to Ben Woelk who manages the group and generously agreed to an interview with us.
A short while ago I stumbled onto the Twitter account of an Information Security Awareness program at my alma mater the Rochester Institute of Technology (RIT). I was immediately impressed by the following they had among their social networks and after digging a bit deeper into their activities I couldn't help but reach out to Ben Woelk who manages the group and generously agreed to an interview with us.  .
. PowerBroker for Windows (PBW) is designed to integrate directly into your corporate Active Directory (AD) structure without modifying your existing schema. In the asset labeled “1” below, an administrator simply loads a Group Policy Option (GPO) snap-in onto an asset that uses the Microsoft Management Console (MMC). The administrator can then create policies and rules [...]
PowerBroker for Windows (PBW) is designed to integrate directly into your corporate Active Directory (AD) structure without modifying your existing schema. In the asset labeled “1” below, an administrator simply loads a Group Policy Option (GPO) snap-in onto an asset that uses the Microsoft Management Console (MMC). The administrator can then create policies and rules [...] Scaling up SaaS is more than just architecture A lot of time and effort went into PowerBroker Mobile as a SaaS solution, we spent a lot of time designing the most scalable, fault resistant system possible. What we came up with was a system that could scale across multiple geographic regions with no single point [...]
Scaling up SaaS is more than just architecture A lot of time and effort went into PowerBroker Mobile as a SaaS solution, we spent a lot of time designing the most scalable, fault resistant system possible. What we came up with was a system that could scale across multiple geographic regions with no single point [...]